Diagnoses and identifies issues within your system network
Are your OS and middleware secure?
Find out by running an assessment to prevent incidents.
In general, installation of anti-virus software and OS update are known as the two effective methods of security measures. However, ways of cyberattacks have been evolving.
The two security measures will not be sufficient to eliminate vulnerabilities such as design flaws, programming errors, and configuration flaws in OS and middleware.
To understand the existing threats and take appropriate measures, vulnerability assessment is a must.
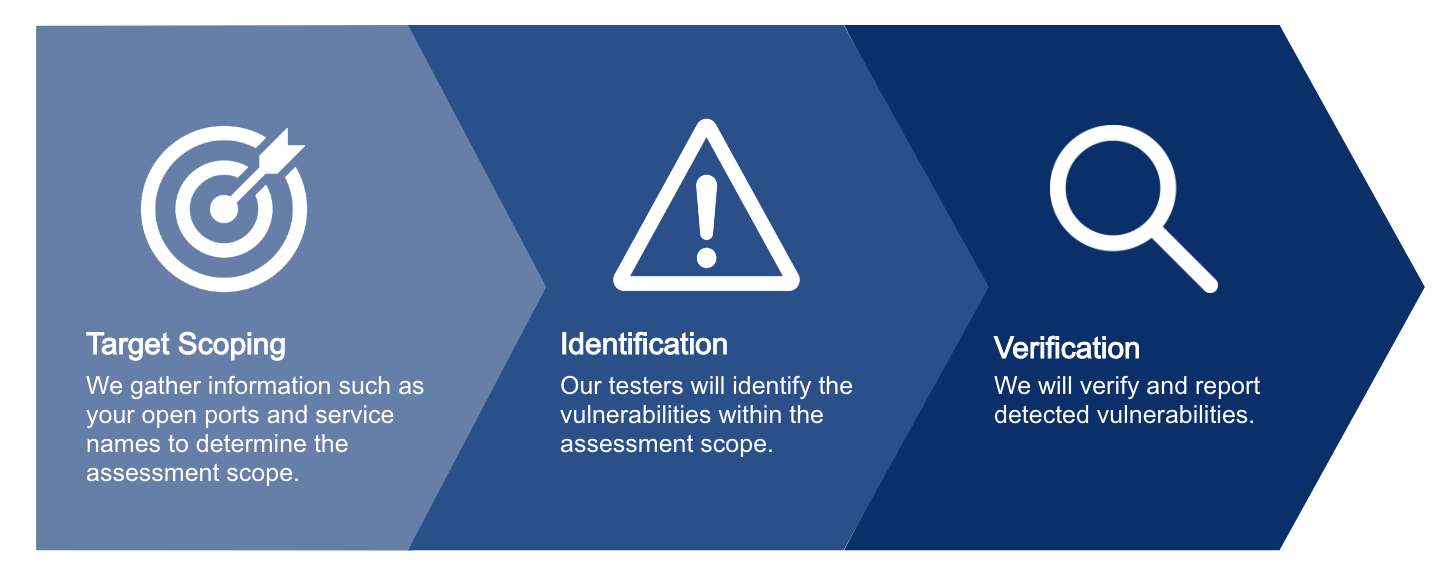
Description
For you to efficiently take security measures, we investigate and report the vulnerability
within your company’s system network.
We Check:
- if your server, network devices, terminals, operating OS, Middleware, server software
connected to your network have unsecure settings - if security patches are applied properly
These vulnerabilities may result in unauthorized intrusions.
Our security engineers will anticipate attacks from various network environments such as
IPv4, IPv6, wireless local area network, internet, internal network, server, and clients. They
will then identify and analyze the vulnerability in your system status (servers, clients, and
network devices) from the attacker’s perspective.
You will receive a report with a list of security measures recommendations suitable for your
working environment. This report can also be used for future risk management.
Examples of detectable vulnerability
-
- Remains of unnecessary open ports
- Anonymous connectivity of FTP server
- Unauthorized mail relay
- DSN construction, defective terminal
- HTTP/HTTPS construction, defective terminal
- Unprepared exposure of RPC information
- SMB construction, defective terminal
- Presence of backdoor port
Assessment Methods
- Onsite assessment
- Remote assessment
Example of assessment subjects
Through the network vulnerability assessment, the following will become clear:
- Existence of known vulnerability within various services (applications)
- Operation service status
- Possible exposure of system information from the banner
- Confirmation of issues due to defective terminal
- Privilege escalation Vulnerability
- Threats to the normal operation
Primary Scanning Items
-
- Port Scan
- ICMP Scan
- OS version
- Operation system version
- Operation system behavior
- Access restriction
- Strength of authentication (default accounts, easy-to-guess accounts)
- Web service behavior
- FQDN
- Behavior of special applications
Optional services
-
- IPv6
- Denial-of-Service (DoS) Attack
- Brute Force (authentication tolerance)
- Diagnostic System Host
- Performance measurement (we measure the processing capability of server and
application through the network) - Nmap Reporter Free(Report creation tool for NMAP port scan)
Our Approach